Marta Marczykowska-Górecka is streamlining Qubes OS device management in the 14th round of the prototype fund. In this guest article, she explains why security and usability isn’t a dilemma, whereas it’s impossible to have one without the other.
It is a universally acknowledged truth that any secure computer program is either confusingly complex or extremely simplified and unable to perform any serious tasks (and probably actually insecure, too). Usability is hard, after all – and worse, it’s often thought to be detrimental to security and actively degrading and detrimental for the user. There’s real Linux, and then there are those unpleasant at best and downright discriminating at worst jokes about how “Ubuntu” means “I don’t know how to install Debian”. If you can’t handle configuring and using OpenPGP, you don’t deserve encrypted emails, and why wouldn’t you just set up your own Nextcloud instance instead of using Google cloud services? This is not a helpful attitude. Fixing usability of open source software will make it more secure for everyone (yes, even the nerds).
I have been working (whenever funding gods smiled at me) on Qubes OS for a couple of years now, and when I started, this attitude was quite prevalent both in our community and in the broader hacker/security/open source communities. Qubes OS is a security-focused operating system – to make a long and complex story short, the idea behind it is: “what if we isolated various parts of your system using virtual machines”. There is a separate virtual machine that serves as a firewall, and one that holds USB controllers so that they can’t just wreak havoc on the rest of the system. You can have an offline password vault virtual machine, and another one that will wipe itself after being closed (think Privacy Mode, but more), and as your USB devices are isolated from everything else, you can even securely see what’s on that one curious USB stick you found at a parking lot. It’s all quite a brilliant idea (at least I think so), but not a simple one. Whenever I raised the idea of making Qubes OS more usable, I encountered resistance. Expert users, hackers, security professionals – they were afraid a usable system wouldn’t be usable for them. Usable – to them – meant having important, everyday functionality hidden behind ten dozen clicks and a condescending wizard. Usable meant big icons that left little space for what they actually wanted to do. Usable was downright derogative.
There is one rote response to those fears:
“But we need to make things usable (that is, simple and pretty), because otherwise nobody will use them and then open source software will die out! Stop complaining, hackers – you will manage with your terminal, your bash scripts and hastily applied self-made patches. Your input is not important in this conversation!”
This is not a helpful way to approach the conversation, though. Moreover, usability is important for everyone – experts and normal users alike. Yes, experienced users who are very invested in using a certain program or an operating system can handle or circumvent many inconveniences that would scare off a less experienced or less involved user, but it does not mean that bad usability has no consequences for them. I like to compare this to a pothole: is a cautious and competent driver able to drive around a pothole? Usually, yes. But this doesn’t mean that fixing potholes is bad, or that even a cautious and competent driver will never damage their car or at least jostle themselves and their passengers around due to a pothole.
Because – and let me let you in on a little secret – experts are human, too. Being a very capable computer user does not mean you are free from various cognitive biases and foibles – and even experts and hackers can be tired, ill or anxious. All humans make mistakes. A secure solution that requires the user to be perfect is, in truth, quite insecure. Users will mess up sometimes, and it’s not the software’s job to act as a strict parent, punishing them for moments of inattention and doling out the reward of security only to the most obedient children. Everybody has the right to secure and private computer use, and it’s not a matter of deserving it through putting enough work in. Usability is and should not be just about making things pretty and simple – it is also, and I would argue especially, about saving users from their own mistakes and making the good (secure and effective) way of using our programs the one that is also the most convenient and pleasant.
Usability is also not about smiplifying things to the point of uselessness. Open source community does need complex, configurable tools that allow users to do everything and a bit – but if using those tools is always cumbersome and time-consuming, they will never be adopted widely, even among experts, even if they offer security and privacy incomparable with any other. If the easiest and fastest way to get a photo from your phone (a.k.a. the most-used photo camera for most people nowadays) to your PC is by sending it to someone via Facebook or using Google Storage, a lot of people, even security-and-privacy conscious people, will choose those solutions at least some of the time. Yes, tools for users who have more relevant knowledge and who want to do more complicated things need configurability and flexibility, but this does not mean they need to be painful to use.
The project I am currently working on under the auspices of Prototype Fund is very much related to those concerns. I want to fix the way device handling is presented in Qubes OS. It doesn’t sound like much of an issue at a first glance – devices? They just happen in the background, right? Except for printers, but nobody likes those anyway. It’s not as simple as that in Qubes OS. The users choose themselves which devices can be accessed by which virtual machine. It is a very powerful security tool – but also a very convoluted UX problem. The “bad UX is bad security” problem raises its head again. The easiest way of using various USB devices in Qubes OS is using them within the dedicated USB virtual machine – they are already there, after all. But this means the user is tempted to do more and more things within that virtual machine, even potentially dangerous things, like opening files from unknown USB sticks or accessing their social media. The whole point of Qubes OS – isolation of different activities into separate virtual machines – becomes moot. So, my goal – making the secure way of using devices as painless as possible – isn’t just something which makes the user feel good – but also secure. Because the lower the cost of making things correctly, the more likely people are to do it. Yes, I would like to make the user interface related to device management look good (also because it is easier to read things when they look nicer – there is psychological research on that) – but the goal of those usability changes is, in the end, security. The best security features are useless, if they are not used. Qubes OS offers more security than most other operating systems – but if it’s used badly due to confusion, bad interface decisions, or even user laziness, the security benefit is significantly decreased.
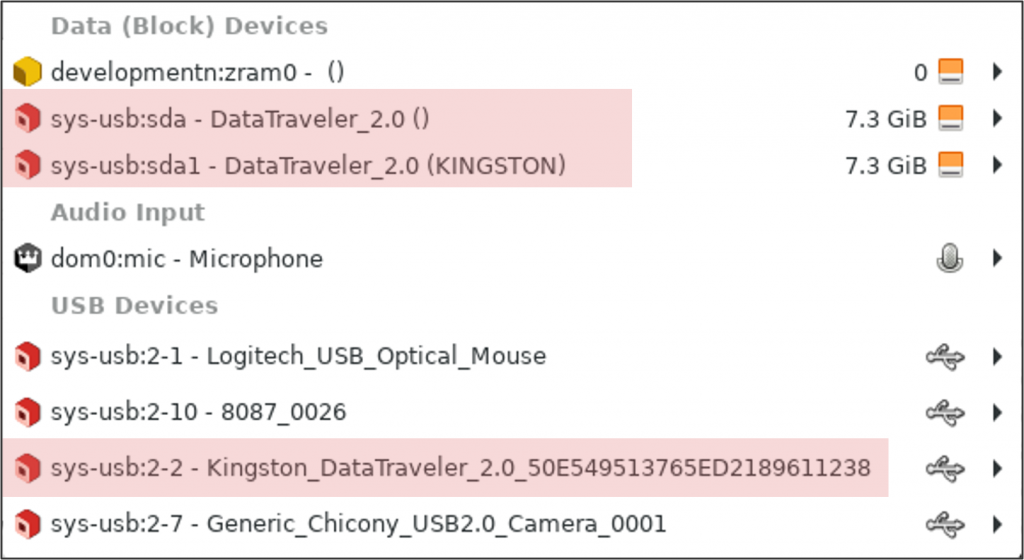
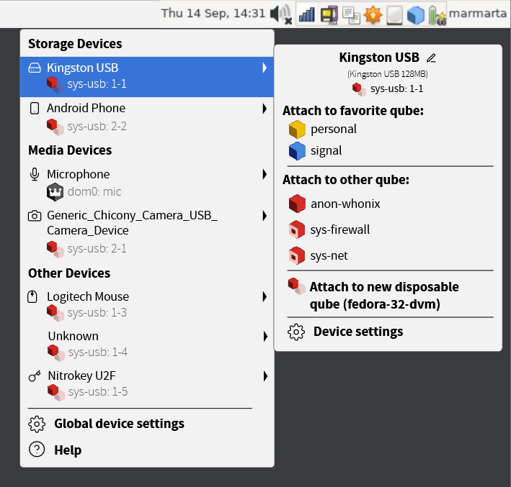
I spend a lot of time working with users: looking how they use Qubes OS, asking what annoys them and what they would improve. One of the questions I asked during this project in particular is about the mistakes users make in device handling – problems like “oops, I assigned the suspicious USB stick to the wrong virtual machine” or “I wanted to detach the device from the virtual machine but instead I attached it to another one”. The goal of my project is redesigning the interface so that those mistakes happen less often. More visual distance between different UX options, more configurability – all those things can reduce risks. Naturally, we cannot and should not protect people from all mistakes – but programs should make it harder to make mistakes , not easier. If you buy a chainsaw, it’ll come with a bunch of safety features, from hand guards to brakes, and in my opinion, computer programs that touch the most important parts of our lives (like operating systems and browsers) should not be less safe to use than a chainsaw.
Open source software is often considered synonymous with bad usability. This reputation is partially an undeserved artifact of times past, partially the fault of funding and personnel woes (user research takes time and requires people who are good at talking to people – not exactly the core competence for software development) – but also partially the fault of ingrained prejudices I discussed above. We are afraid of dumbing down our software, of turning into some guided MacOS experience that allows you to do only a limited number of things, and driven by this apprehension, we often decide that usability is not worth the time. After all, experts will manage, and other people should just learn how to do better. But we are all humans and we all make mistakes. Good usability can help us make fewer of those. It’s not a waste of time, it is crucial for open source success – let’s get to work!
Marta Marczykowska-Górecka is a Software Developer and UX Designer from Berlin. After getting a degree in Psychology and bouncing from one interesting job to another, she found her home in the open source community and has been working on Qubes OS since 2017.